NFT-Based Identity: The Future of Secure Digital Verification
Introduction
In the age of constant data breaches and fragmented login systems, users demand control over their digital identities. NFT-based identity is emerging as a powerful solution, offering secure, verifiable, and self-owned credentials on the blockchain. These identity NFTs are transforming how individuals prove who they are online, without relying on centralized authorities.
What Is NFT-Based Identity?
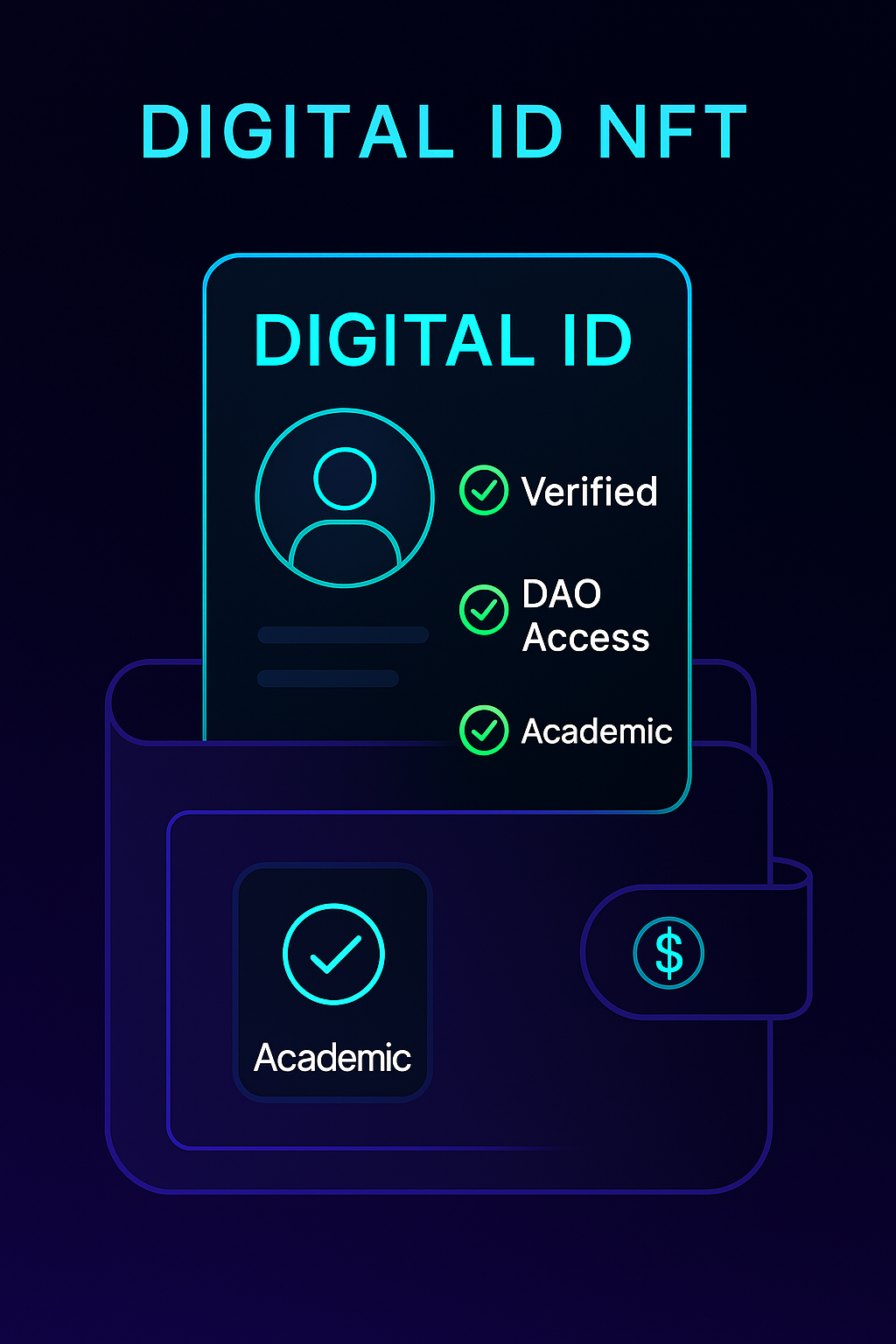
NFT-based identity refers to using non-fungible tokens to represent and verify personal or professional credentials. Unlike typical NFTs used for art or gaming, identity NFTs are often non-transferable (also called soulbound) and contain:
- Personal identifiers
- Academic or professional credentials
- Membership details
- Access rights or KYC data
These NFTs act as digital passports, stored in wallets, accessed across platforms, and verified without third-party gatekeepers.
Why the Shift to Decentralized Identity?
Traditional identity systems rely on central entities: governments, banks, universities, and platforms. Users must repeatedly prove who they are, share sensitive data, and trust intermediaries to keep it safe.
NFT-based identity solves this by:
- Putting users in control of their credentials
- Enabling seamless verification across apps and platforms
- Reducing the need for re-verification every time someone signs up
- Improving privacy by allowing selective disclosure of information
This shift supports a more secure, flexible, and user-centric web.
ALSO READ
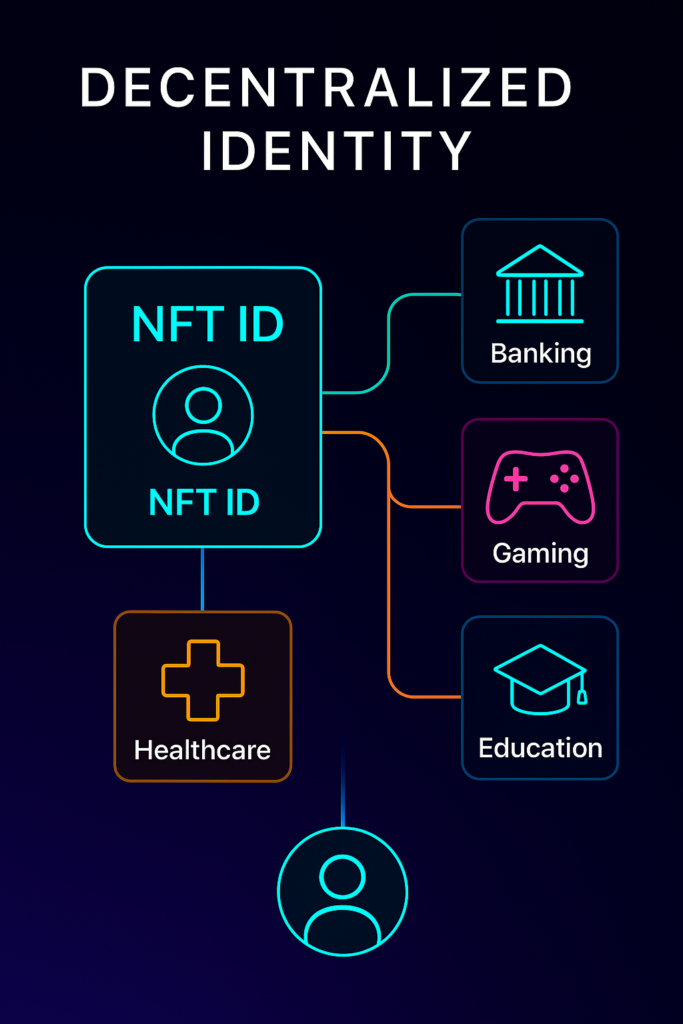
Key Use Cases of NFT Identity Systems
NFT identity models are being tested across sectors. Here’s where they are gaining traction:
1. Academic Credentials and Certification
Universities are issuing NFT-based diplomas and course certificates. These credentials are immutable, easily shareable, and fraud-proof.
- MIT, Stanford, and others are piloting blockchain degrees
- Employers can verify authenticity with a single click
- No need for paper copies or email confirmation chains
2. On-Chain KYC and Access Control
Web3 platforms are adopting NFT-based identity for seamless KYC:
- Users mint identity tokens after verifying once
- Access to DeFi, exchanges, or gated content is linked to the NFT
- Compliance becomes easier without storing sensitive data centrally
This ensures both convenience and security without exposing raw personal data every time.
3. DAO Memberships and Voting Rights
Decentralized autonomous organizations use identity NFTs to manage:
- Voting eligibility
- Contribution records
- Role-based access to projects or tools
Each NFT represents a user’s standing within the organization, keeping governance transparent and fair.
4. Medical and Health Data Ownership
In healthcare, NFT-based identities could give patients full ownership of their records:
- Minted NFTs point to encrypted health data
- Access is granted to doctors or insurers only when needed
- Data stays private, but verifiable
This model offers a safer alternative to centralized medical databases prone to breaches.
5. Gaming and Virtual Identity
Gamers are using NFTs as persistent identity markers across platforms:
- A single identity NFT stores avatar traits, in-game history, and rankings
- Transferring reputation between games becomes possible
- Customizations and skins remain linked to the user, not the game
This creates a sense of continuity and ownership in digital worlds.
Benefits of NFT-Based Identity
There are strong incentives for both users and platforms to adopt NFT-based identity systems:
- Ownership: Users control their credentials, not corporations
- Security: Data is harder to tamper with or steal
- Interoperability: One NFT works across multiple services
- Privacy: Share only what’s necessary, not your entire identity
- Efficiency: No repeated KYC or account creation needed
These benefits align with the Web3 vision of decentralized, user-first digital interaction.
Challenges and Considerations
Despite its potential, NFT-based identity must navigate key concerns:
- Loss of wallet access: Losing an identity NFT could lock out essential services
- Privacy vs permanence: Storing personal info on-chain requires careful encryption
- Standardization: Different platforms use varying formats and rules
- Adoption barriers: Non-crypto users may struggle with wallet setup or token concepts
To address these issues, developers are exploring encrypted metadata, recovery protocols, and user-friendly onboarding flows.
Future Outlook: Identity in Web3 and Beyond
NFT-based identity is still in early stages but advancing quickly. In the coming years, expect to see:
- Soulbound credentials becoming default for education and employment
- Cross-platform IDs that work from Discord to financial services
- Government-led NFT IDs for licenses, benefits, or citizenship
- AI-linked identity NFTs that adapt to usage and trust metrics
Eventually, identity will feel frictionless yet secure, no more endless forms, no more repeated verifications, just ownership and trust.
Conclusion
NFT-based identity systems offer a smarter, safer way to verify who we are online. Whether unlocking services, proving credentials, or joining communities, these tokens give users control while boosting trust. As the digital world expands, identity must evolve, and NFTs are leading the charge.
Call to Action
🎯 Ready to explore NFT-based identity for your app or platform? Download our NFT Identity Integration Blueprint to get started with tools, security practices, and real-world use cases.